Abstract: HTTP Live Streaming (abbreviated as HLS) is an HTTP-based streaming media network transport protocol proposed by Apple. Today, some of its principles are mainly centered on the HLS protocol.
Introduction to HLS ProtocolHTTP Live Streaming (abbreviated as HLS) is an HTTP-based streaming media network transport protocol proposed by Apple. It is part of Apple's QuickTIme X and iPhone software systems. It works by dividing the entire stream into small, HTTP-based files for download, each time only downloading some. When the media stream is playing, the client can choose to download the same resource at different rates from many different alternate sources, allowing the streaming session to adapt to different data rates. When starting a streaming session, the client downloads an extended M3U (m3u8) playlist file containing metadata for finding available media streams.
HLS only requests basic HTTP messages. Unlike Real-Time Transport Protocol (RTP), HLS can pass through any firewall or proxy server that allows HTTP data to pass. It is also easy to use a content distribution network to transport media streams.
Apple has submitted the HLS protocol as an Internet draft (phased submission) and has been submitted to the IETF as an informal standard in the first phase. However, even if Apple occasionally submits some minor updates, the IETF has no further actions regarding the development of this standard.
HLS overall architecture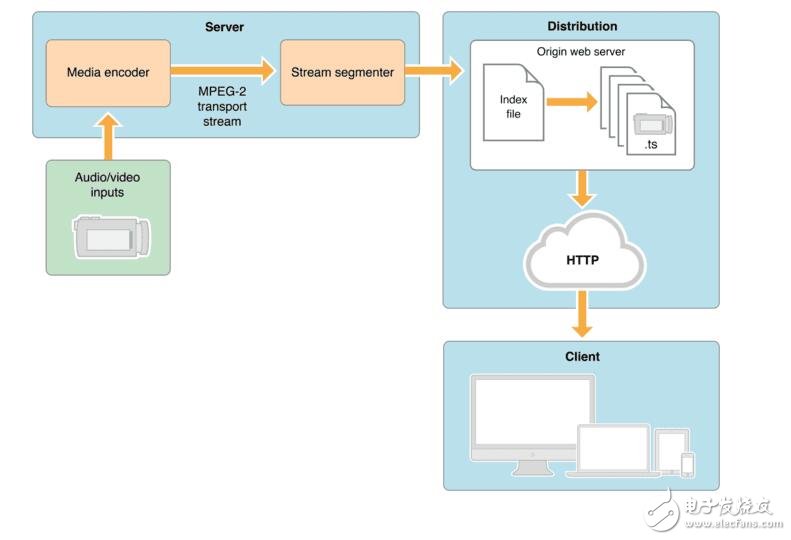
The above is the overall architecture diagram of HLS. It can be seen that there are three parts in total: Server, CDN, Client.
HLS agreement requirements1. The package format of the video is TS.
2. The encoding format of the video is H264, and the audio encoding format is MP3, AAC or AC-3.
3. In addition to the TS video file itself, an m3u8 file (text file) for controlling playback is also defined.
Why Apple wants to propose the HLS agreement, in fact, his main purpose is to solve some problems in the RTMP protocol. For example, the RTMP protocol does not use the standard HTTP interface to transmit data, so it may be blocked by the firewall in some special network environments. However, because HLS transmits data due to the HTTP protocol used, it will not be blocked by the firewall (it will not be blocked by the firewall even with the 80 interface).
Also under load, RTMP is a stateful protocol that makes it difficult to scale smoothly the video server because it needs to maintain state for each client that plays the video stream. While HLS is based on stateless protocol (HTTP), the client simply downloads the normal TS files stored on the server in order, and it is as simple as balancing the load as a normal HTTP file server.
In addition, the HLS protocol itself achieves rate adaptation, and devices with different bandwidths can automatically switch to the video playback that best suits their own bit rate. In fact, the biggest advantage of HLS is that his relative is Apple. Apple only provides native support for HLS on its own iOS device and gives up flash. Android is also forced to support HLS by Pingguo’s “Kuanweiâ€. In this way, flv, rtmp these Adobe video solutions need extra effort to play on mobile devices. Of course, the huge performance pressure caused by flash on mobile devices is also a problem of its own.
However, HLS also has some pits that cannot be crossed. For example, the video delay time of live broadcast using HLS protocol cannot be less than 10 seconds, and the delay of RTMP protocol can be as low as 3 or 4 seconds. Therefore, please be cautious with HLS for services that are sensitive to live broadcast delays.
HLS request process:1 http requests the url of m3u8.
2 The server returns a playlist of m3u8. This playlist is updated in real time, and the url of 5 pieces of data is generally given once.
3 The client parses the playlist of m3u8, and then requests the url of each segment in order to obtain the ts data stream.
RSA implementation details key generationFirst, a probabilistic algorithm is used to verify that a large integer generated randomly is a prime number. Such an algorithm is faster and can eliminate most non-prime numbers. If a number passes this test, then use an exact test to ensure that it is indeed a prime number.
In addition, the p and q thus found must meet certain requirements. First, they should not be too close. In addition, the factor of p-1 or q-1 should not be too small, otherwise N can be quickly decomposed.
In addition, the algorithm for finding prime numbers does not give the attacker any information. How these prime numbers are found, especially the software that generates random numbers must be very good. The requirements are random and unpredictable. These two requirements are not the same. A random process may produce a series of uncorrelated numbers, but if someone can predict (or partially predict) the series, then it is already unreliable. For example, there are some very good random number algorithms, but they have all been published, so they can't be used, because if an attacker can guess half of p and q, then they can easily figure out the other half. .
In addition, the key d must be large enough. In 1990, it was proved that if p is greater than q and less than 2q (which is a very frequent case), then n and e can be effectively derived from D. Also e = 2 should never be used.
calculating speedSince the calculations are all large numbers, the fastest situation of RSA is several times slower than DES, whether it is software or hardware implementation. Speed ​​has always been a flaw in RSA. Generally used only for a small amount of data encryption. RSA is about 1000 times slower than symmetric cryptographic algorithms that correspond to the same security level.
RSA is much slower than DES and other symmetric algorithms. In fact, Bob generally uses a symmetric algorithm to encrypt his information, then uses RSA to encrypt his relatively short symmetric cipher, and then sends a symmetric cipher encrypted with RSA and a message encrypted with a symmetric algorithm to Alice.
In this way, the requirement for random numbers is higher, especially for the generation of symmetric ciphers, because otherwise the symmetric cipher can be directly attacked over the RSA.
Key distributionAs with other encryption processes, the process of assigning a public key to RSA is very important. The process of assigning a public key must be able to withstand an attack that is replaced by it. Suppose Eve gives Bob a public key and makes Bob believe that this is Alice's public key, and she can intercept the information transfer between Alice and Bob, then she can pass her own public key to Bob, Bob thinks this Is Alice's public key. Eve can intercept all the messages that Bob passed to Alice, decrypt the message with her own key, read the message, and then encrypt the message with Alice's public key and pass it to Alice. In theory, neither Alice nor Bob will find Eve listening to their messages. Today, people generally use digital authentication to prevent such attacks.
RSA disadvantage1) It is very troublesome to generate a key, which is limited by the technique of prime number generation, and thus it is difficult to achieve one time and one secret.
2) Security, the security of RSA depends on the factorization of large numbers, but it does not theoretically prove that the difficulty of deciphering RSA is equivalent to the difficulty of large number decomposition, and most people in cryptography tend to factorize not NP.
3) The speed is too slow. Because the RSA packet length is too large, n must be at least 600 bits or more for security. This makes the operation costly, especially slower, which is several orders of magnitude slower than the symmetric cipher algorithm. With the development of large number decomposition technology, this length is still increasing, which is not conducive to the standardization of data formats.
RSA securityFirst, let's explore why the RSA password is difficult to crack?
In the RSA password application, the public key KU is public, ie the values ​​of e and n can be obtained by third party eavesdroppers. The problem of cracking the RSA password is to find the value of d from the known values ​​of e and n (n is equal to pq), so that the private key can be obtained to crack the ciphertext. From the above formula: d ≡e-1 (mod((p-1)(q-1)))) or de≡1 (mod((p-1)(q-1)))) we can see. The essential problem of password cracking is to find (p-1) and (q-1) from the value of Pq. In other words, as long as the values ​​of p and q are found, we can find the value of d and get the private key.
When p and q are a large prime number, it is a recognized mathematical problem to decompose the factors p and q from their product pq. For example, when pq is as large as 1024 bits, no one has been able to use any calculation tool to complete the task of decomposition factor. Therefore, RSA has been tested for various attacks for nearly two decades, and has gradually been accepted by people. It is generally considered to be one of the best public key schemes at present.
However, although the security of RSA relies on the factorization of large numbers, it does not theoretically prove that the difficulty of deciphering RSA is equivalent to the difficulty of large number decomposition. That is, the major flaw of RSA is that it cannot theoretically grasp its confidentiality.
In addition, the shortcomings of RSA are: A) It is very troublesome to generate a key, which is limited by the technique of prime number generation, and thus it is difficult to do it once and for all. B) The packet length is too large. To ensure security, n must be at least 600 bits or more, which makes the operation costly high, especially the slower speed, which is several orders of magnitude slower than the symmetric cryptographic algorithm; and with the development of the large number decomposition technique This length is still increasing, which is not conducive to the standardization of data formats. Therefore, using RSA can only encrypt a small amount of data, and a large amount of data encryption depends on a symmetric cryptographic algorithm.
10-inch tablet devices have greatly surpassed netbooks in terms of entertainment, including reading, games, and audio-visual enjoyment. In other respects, the basic operation of the 10-inch tablet computer built on the touch screen ensures that the application of the tablet computer can be well realized, and its operation performance is closer to that of a smartphone.
1.In appearance, the 10-inches tablet computer looks like a large-screen mobile phone, or more like a separate LCD screen.
2.In terms of hardware configuration, the 10-inches tablet computer has all the hardware devices of a traditional computer, and has its own unique operating system, compatible with a variety of applications, and has a complete set of computer functions.
3.The 10-inches tablet computer is a miniaturized computer. Compared with traditional desktop computers, tablet computers are mobile and flexible. Compared with Laptops, tablets are smaller and more portable
4.The 10-inches tablet is a digital notebook with digital ink function. In daily use, you can use the tablet computer like an ordinary notebook, take notes anytime and anywhere, and leave your own notes in electronic texts and documents.
10 Inches Tablet Pc,Tablet Pc Android,10 Inch Quad Core Tablet,Tablet 10 Inch
Jingjiang Gisen Technology Co.,Ltd , https://www.gisentech.com