Do you clearly understand the industrial structure of industrial information security?
This is a required course for practitioners.
With the rapid development of a new generation of information technology, the industrial information security industry structure is constantly changing, the boundaries between software and hardware products are becoming more and more blurred, and products and services are more closely connected.
Compared with traditional computer network security, industrial information security has particularities in terms of guarantee objects, security requirements, network and device environment, communication protocols, etc. Identifying the risks and hidden safety hazards in the information systems of industrial enterprises, and correspondingly implementing corresponding security technologies and management guarantee strategies are important means to ensure the security of industrial information.

Based on the reference of Gartner and ARC consulting companies to classify the main products and services of the market, combined with my country's actual situation, and based on mainstream market applications, the "China Industrial Information Security Industry Development White Paper" will comb the industrial structure in detail.
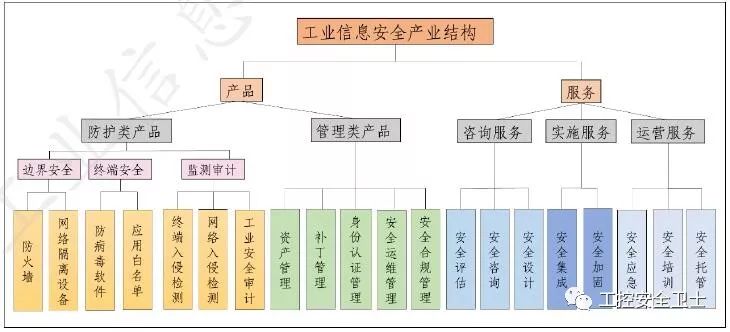
Product category
From the perspective of market development, in view of the information security needs of industrial enterprise users, the structure of industrial information security products is mainly divided into two categories: protection and management.
From the perspective of technical protection, industrial information security protection products mainly include border security products, terminal security products and monitoring and audit products. Among them, border security products are represented by industrial firewalls and network isolation devices, which are mainly used to protect the borders of industrial networks and provide regional isolation; terminal security products cover security products that can protect all terminal devices in an industrial information security environment, such as Virus software, application whitelist, port device control, main hardening, etc .; monitoring and auditing products are mainly used to monitor and evaluate the integrity of industrial control systems. Typical products include terminal intrusion detection, network intrusion detection, and industrial security auditing.
From the perspective of security strategy and management process, industrial information security management products include asset management, patch management, identity certification management, security operation and maintenance management and security compliance management, designed to help companies manage and maintain industrial assets and equipment Security posture.
Since the security needs of industrial enterprise users focus on the reliability of production and operation processes, industrial information security management products combine traditional IT network security management products and solutions, but limit the functional modules that will affect the industrial production environment. At the same time, industrial information security management products will also extend coverage to other industrial assets and control protocols.
Service
Industrial information security services mainly refer to third-party security services purchased by industrial enterprises.
Through the analysis of the driving factors of the development of the industrial information security service market, security services can be divided into three categories according to the security service objects and the life cycle of enterprise user project management.
The first type is consulting services represented by security assessment, security consulting, and security design. This type of service mainly relies on the knowledge system and industry experience of experts, and establishes an industrial information security management system for users based on domestic and foreign standards and industry regulatory standards. Provide decision-making basis and optimization plan.
The second category is the implementation services represented by security integration and security hardening. These services mainly adopt appropriate management processes and control measures, and implement industrial information security management systems through products and solutions.
The last category is the operation services represented by safety emergency, safety training and safe trusteeship, aiming to provide services for industrial enterprises to meet their full life cycle safety operation and management needs.

The industrial form has taken shape, ready for the shovel to start panning for gold!
Features
â—† Wide Application
Specialized in Hairdryer Switch with crisp handfeel,clear gears,reliable electrical contact
â—† Easy to install and use
Simple installation, freely turn on or off the load which you want to control.
â—† High Operating Life
Made of high quality polyamide eP(Nylon PA66) material, this sturdy mini boat Rocker Switch is born for anti-corrosion,anti-acid and high resistant with silver terminals.100,000 times of ON/OFF operating life span.
Automotive Rocker Switch,Dual Rocker Switch,Red Rocker Switch,Custom Automotive Rocker Switches
Ningbo Jialin Electronics Co.,Ltd , https://www.donghai-switch.com