A lot of friends who use Windows 10 often encounter such a situation. The computer suddenly appears with a flashing window with a screen. It is too late to see what it is and disappears again. The same situation will happen again at different times. Repeatedly appears. So what is the program running in the background? Find out why and solve it for everyone.
Analysis of Causes to Find Out Inside the Ghost
From the fault phenomenon, because this is a regular occurrence, it is very consistent with the characteristics of the background system planning tasks. Since there is no current window, these background programs are mostly command lines, so the performance on the screen is flash. Of course, the situation of poisoning is not ruled out, so if this happens, first of all anti-virus software will be upgraded to the latest virus database for killing. If there is no virus, you can start with the mission plan.
In-system detection event viewer determines the cause
Since it is a scheduled task running in the background of the system, the "Event Viewer" provided by Windows 10 can record the running status of these tasks. However, by default, Windows 10 does not open a record of scheduled tasks, so you need to open it yourself.
Enter "Scheduled Tasks" in the taskbar search box to open the Task Scheduler Manager. Click “Enable all task history†under “Operation†on the right side of the window (it will be displayed as “Disable all task historyâ€), so that the system schedule task will be automatically recorded by the event viewer (Figure 1).
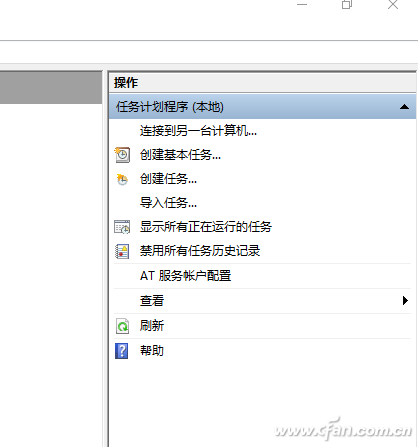
Figure 1 Open Schedule Task Record
Now is to continue your daily operation and wait for the above mysterious window to be displayed again. At this point in the taskbar search window enter the "Event Viewer", start the program and then expand "Applications and Services Logs → Microsoft → Windows → TaskScheduler → Operational", in the right window according to the window appears time to filter, you can see the author computer The window that appears on the screen is caused by a scheduled task named "OfficeBackgroundTaskHandlerRegistration" (Figure 2).
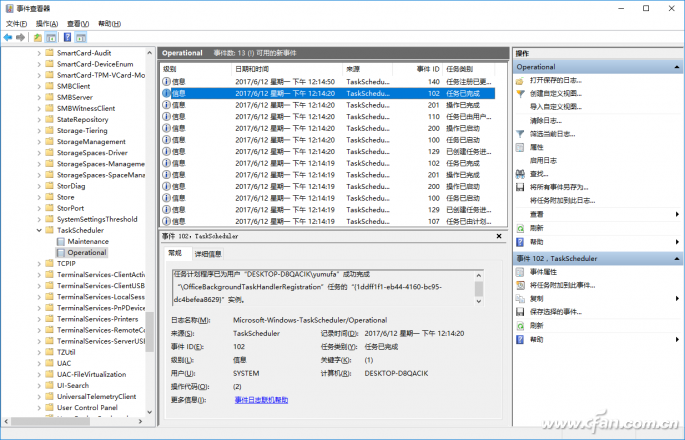
Figure 2 Viewing activated scheduled tasks
hint:
After the recording of scheduled task events, many recorded events will appear in the system. You can customize the search based on the event source, user, etc., depending on when the scheduled task occurs, or click Filter in the right pane.
By the time of the window and the recording time of the scheduled task, we can basically conclude that the window appears due to the "OfficeBackgroundTaskHandlerRegistration" scheduled task. However, since this window appears and disappears quickly, in order to further determine whether it is caused by the planned task, we can also use the "oCAM" screen recording software for recording. Start "oCAM" and click on "Menu → Options". The number of video recording frames is selected to be 30 or more (larger frames can be used to record those windows that are flashed across). Return to the main window Click "recording area" to select full-screen recording, do not record sound, and then click "record" (Figure 3).
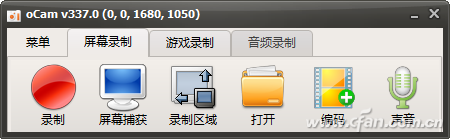
Figure 3 Start Recording Screen
After waiting for the mysterious window to reappear, the recording stops. After the window is recorded, the default recorded video is saved in the software installation directory. Follow the prompts to open the movie and TV. Click pause when a pop-up window appears. Fast-forward and rewind, you can see this pop-up window running exactly the above-mentioned scheduled tasks (Figure 4).
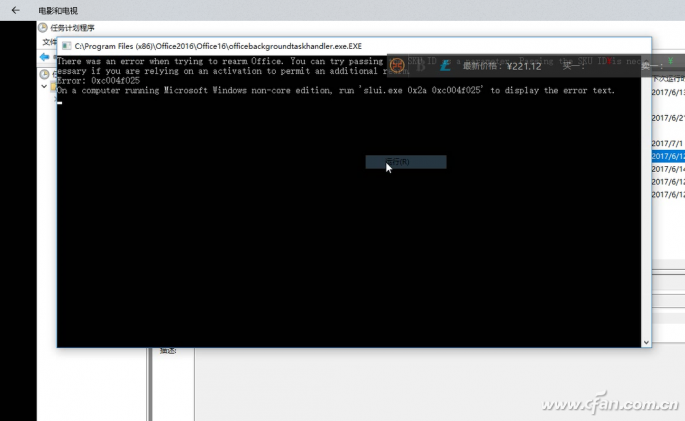
Figure 4 Viewing recorded popups
Know the culprit of the pop-up window, then we can set according to their actual needs. Open the Task Scheduler Manager and open it, then expand "Task Schedule Runtime". Here, all scheduled tasks running on the machine will be displayed. You can search by the name shown above (Figure 5).
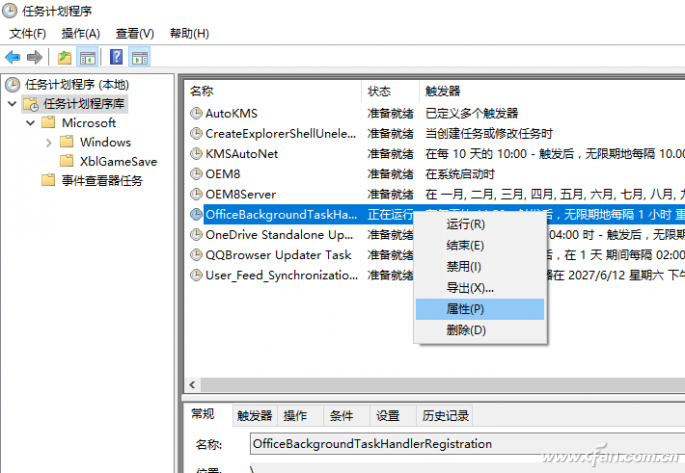
Figure 5 Viewing the task plan runtime
If you find an unfamiliar virus program here, end the running of its task, then open the task plan properties window, switch to "operations", you can see the details of the running program, delete the file as prompted, and finally in " Task Schedule Runtime" to delete its task (Figure 6).
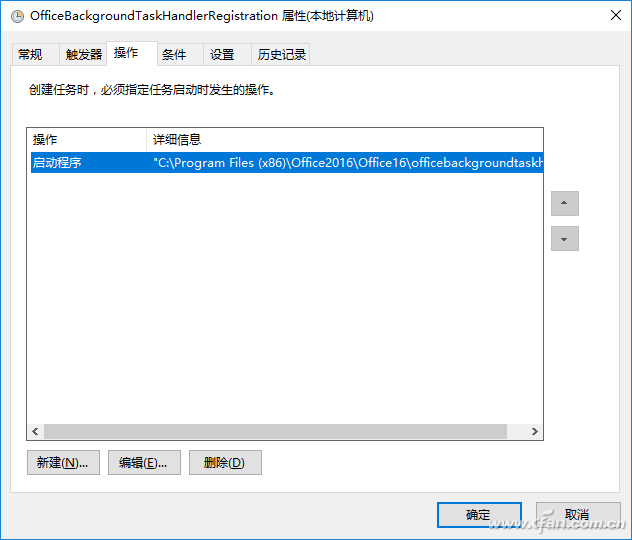
Figure 6 Viewing task properties
If it is a normal system scheduled task, we can make it run silently in the background by changing the way the account runs. Open the Task Schedule Properties window as above, switch to "General", click "Change User or Group", enter "SYSTEM" in "Enter the object name to be selected", and let the task run as SYSTEM account (Figure 7).
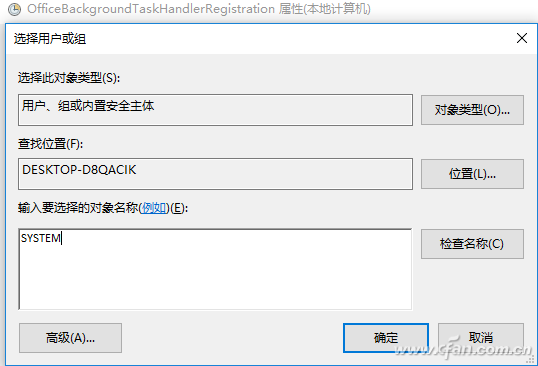
Figure 7 Change Run Account
Return to the Properties window. Check “Run with maximum privileges†(to prevent the running program from needing higher permissions, resulting in the UAC window popping up). Now the scheduled task running account has been changed to “NT AUTHOTY\SYSTEM†because the SYSTEM account is a system built-in account. And it does not have an operating environment, so the above schedule task will run silently in the background and no more annoying running windows will pop up (Figure 8).
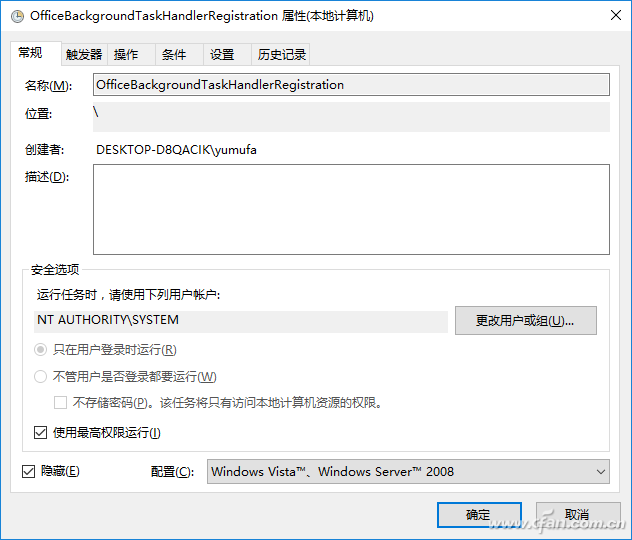
Figure 8 Successfully changing the running account
hint:
Some viruses also use the SYSTEM identity to run silently in the background. For such suspicious program tasks, we can change their running identity to the current account. In this case, the virus will be intercepted by UAC at runtime. We can use the UAC prompt to perform the judgment procedure again. Is it harmful?
Application-Specific Integrated Circuit refers to an integrated circuit specifically designed to perform a specific computing task. It is very common to use ASIC for mining in the field of blockchain. This article will analyze the principle of ASIC mining and why it should be anti-ASIC.
For Bitcoin, mining has gone through four stages: CPU, GPU, FPGA and ASIC. GPU is naturally suitable for parallel simple operations, so the execution of SHA256 is much higher than the CPU. FPGA is a programmable hardware, because it has a certain degree of universality, so the unit price will be relatively expensive. ASIC has a large initial design investment, but the unit price will be cheaper after mass production. Therefore, if you can determine that the market size is relatively large, the use of ASIC technology will be the most cost-effective.
This is the basic principle of ASIC.
In a nutshell, mining is running complicated calculations in the search for a specific number. Whether it`s an ASIC miner or a GPU mining rig, mining hardware must run through many calculations before finding that number. In proof of work systems like Bitcoin, the first one to find that number gets a reward - at the time of writing, 12.5 Bitcoins worth around $96,850. That reward will fall to 6.25 Bitcoins in May 2020.
There are so many people and powerful computing systems trying to mine Bitcoin that miner groups form to find that number and share the profit. Even more, the faster your hardware, the more you earn. That`s why people who can afford it opt for ASIC miners because it gives them the greatest chance of earning cryptocurrency in exchange for their investment.
Each cryptocurrency has its own cryptographic hash algorithm, and ASIC miners are designed to mine using that specific algorithm. Bitcoin ASIC miners are actually designed to calculate the SHA-256 hash algorithm. In the case of Litecoin, it uses Scrypt. That means technically they could mine any other coin that`s based on the same algorithm, though typically, people who buy ASIC hardware designed for Bitcoin mine that specific digital currency.
Antin S19J Pro 96Th,Antin S19J Pro,S19J Pro 96T Antminer,s19j pro antminer,s19 xp antminer
Shenzhen YLHM Technology Co., Ltd. , https://www.ylhm-tech.com